How to Upload Configure to Palo Alto Firewall
Palo Alto Firewall (Version four)
The purpose of this document is to detail the installation and configuration of an Uplogix Local Manager (LM) to manage and facilitate remote connectivity to a Palo Alto firewall.
Features
Supports Palo Alto firewalls running PAN-Bone version 4 or higher.
Physical Connection
Connect a costless serial port on the Local Managing director to the Palo Alto'south RS-232 console management port with a standard Cat-5 cablevision.
Recommended Configuration
For proactive monitoring of the Palo Alto'south status, and to ensure the availability of backup configurations, it is recommended that:
- The Local Manager serial port connected to the Palo Alto is configured via the config init control.
- Automated backup of the configuration is scheduled.
- Tthe paloAltoStatus ruleset is scheduled
Configuring the Port
To configure the Local Managing director for connexion to a Palo Alto firewall, navigate to the port that the Palo Alto is continued to, run the command config init, and follow the prompts every bit below (substituting your Palo Alto'due south IP accost):
[admin@UplogixLM (port1/iv)]# config init --- Enter New Values --- clarification: Palo Alto firewall make [native]: enhanced direction IP: 203.0.113.16 Configure dedicated ethernet port? (y/north) [north]: control prompt [[#>]]: login prompt [(ogin:\southward]: (?<!(?:ast|uccessful)\s)[lL]ogin:\s password prompt [assword:\s]: Password:\s logout command [exit\r]: wakeup command [\r]: panel username []: admin console password []: ******** confirm password []: ******** Serial Bit Rate [9600]: Series Information Fleck [8]: Serial Parity [none]: Serial Stop Chip [1]: Serial Catamenia Control [none]: Do you want to commit these changes? (y/n): y Testing login volition have a few moments... Login successful; credentials are valid. Scheduling default jobs Testing job rulesMonitor Task rulesMonitor was successful Job rulesMonitor was scheduled The default console settings for the Palo Alto firewall are 9600 bit rate, viii serial data bit, no serial parity, serial finish bit i, and no flow command.
Managing Configurations
Back up Configuration
The Uplogix Local Manager can save upwards to twenty backup images on its file arrangement for use in restoring a configuration or pushing a configuration to a new Palo Alto. The file tin be transferred to the LM via TFTP or SCP.
To save the Palo Alto's configuration to the LM, navigate to the port that the Palo Alto is continued to and run the either of the following commands, substituting the LM'southward IP accost:
pull sftp -file running-config.xml "scp export configuration from running-config.xml to ${user}@${ip}:${path}" running-config current pull tftp "tftp consign configuration to 10.0.1.2 from running-config.xml" running-config.xml running-config current Case: [admin@UplogixLM]# port one/4 Palo Alto firewall [admin@UplogixLM (port1/4)]# pull tftp "tftp export configuration to 10.0.1.2 from running-config.xml" running-config.xml running-config electric current Automatic Configuration Backup
To configure the Local Managing director to back upward the running-config of a Palo Alto firewall every three hours, apply i of the following commands:
config schedule pullSftp -file running-config.xml "scp export configuration from running-config.xml to ${user}@${ip}:${path}" running-config current -d 10800 config schedule pullTftp "tftp consign configuration to 10.0.ane.2 from running-config.xml" running-config.xml running-config current -d 10800 Restore Configuration
At that place are multiple steps to restore a backup configuration to a Palo Alto firewall. The file may exist transferred via SCP or TFTP.
Showtime, navigate to the port the Palo Alto is continued to and stage the file to be restored as a candidate configuration:
[admin@UplogixLM (port1/4)]# copy running-config previous candidate Next, run one of the post-obit commands, substituting the LM'due south IP accost for ten.0.1.2:
push button sftp -file running-config.xml "scp import configuration ${user}@${ip}:${path} \r configure \r load config from running-config.xml \r commit \r exit" running-config candidate push tftp "tftp import configuration x.0.1.2/running-config.xml \r configure \r load config from running-config.xml \r commit \r exit" running-config.xml running-config candidate Upon entering 1 of those commands, the Uplogix LM will connect to the Palo Alto's CLI, transfer the candidate configuration, and apply the configuration.
Monitoring Palo Alto Status
Palo Alto Health Check Ruleset
The Local Manager tin exist configured to monitor the status of a managed Palo Alto using the paloAltoStatus rule set. The LM will check the Palo Alto for environmental alarms and high CPU usage. High CPU usage or system oestrus volition trigger an alarm on the LM.
To load the paloAltoStatus dominion fix on the LM, copy and paste the following into the LM at the system level:
config rule no paloAltoChassisPoll config rule paloAltoChassisPoll description - ruleset to query Palo Alto for CPU info, ecology alarms, etc. conditions console.dsr equals true AND console.cts equals true leave action clearValue monitor cpuUse activeness clearValue monitor envAlarm activeness execute -setValue monitor envAlarm $i -design "(True)" -command "prove organization environmentals thermal \r " -raw action execute -setValue monitor cpuUse $1 -blueprint "(\d?\d)\.\d%united states of america" -control "show organisation resource \r q " -raw exit config rule no paloAltoEnvironmentalAlarm config dominion paloAltoEnvironmentalAlarm clarification - sends an warning when "show organization environmentals" returns "true" for an alert state conditions compare-value monitor envAlarm = Truthful get out action alarm GENERIC -a "system hot" action writeStatus hot exit config dominion no paloAltoCPUAlarm config rule paloAltoCPUAlarm clarification weather condition compare-value monitor cpuUse >= 80 get out activeness alarm CPU_LOAD_MAJOR -a "CPU load high" action writeStatus CPU high get out config rule no paloAltoNoResponse config rule paloAltoNoResponse description - when the response to the CPU check has been nil for iii minutes, report an inability to get a resposne weather Not has-value monitor cpuUse AND NOT has-value monitor envAlarm go out activeness alert GENERIC -a "device non responding to CPU and environmental checks" activity writeStatus no response exit config rule no paloAltoSerialDisconnected config rule paloAltoSerialDisconnected description conditions Non console.dsr equals true AND NOT console.cts equals true exit action warning GENERIC -a "series cable unplugged or device powered down" activeness writeStatus no connection exit config ruleset paloAltoStatus rules paloAltoChassisPoll | paloAltoSerialDisconnected | paloAltoNoResponse | paloAltoCPUAlarm | paloAltoEnvironmentalAlarm go out leave To configure the LM to utilize the paloAltoStatus rule set up to monitor a Palo Alto firewall, navigate to the port that the Palo Alto is connected to and run the post-obit command:
config monitor chassis paloAltoStatus Connecting to the Web Interface
Port Forwarding
The Local Director can facilitate connections to the Palo Alto's web interface using the port forwarding characteristic. Run configure protocol forwards on the port the Palo Alto is connected to and add an entry as below:
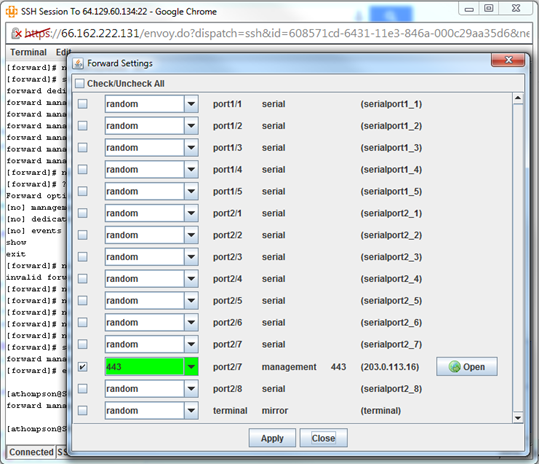
[admin@UplogixLM (port1/4)]# config protocol forward [forward]# management 443 https [forward]# go out Users may now connect to the web interface through an SSH tunnel using the port forwarding feature. In SSh applet on the Control Center, click Terminal, and then Frontwards. Select the Palo Alto's port, enter 443 for the port number, and click Apply. At present, port 443 on 127.0.0.1 on your workstation will connect through the SSH tunnel created past the LM to the web interface on the Palo Alto.
Source: https://uplogix.com/docs/6.1/local-manager-user-guide/configuration-guides/palo-alto-firewall
0 Response to "How to Upload Configure to Palo Alto Firewall"
Post a Comment